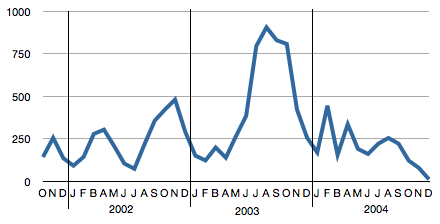
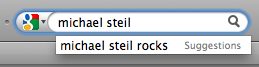
The Easter Egg in the “Schrott-Tornado” at the Deutsches Museum

The Deutsches Museum in Munich (Germany) has a new art installation as part of the reopened Electronics exhibition: The “Schrott-Tornado”, a tornado-shaped sculpture made from scrap electronics. There is (at least) one item in it that is most definitely not trash.